Blog Posts
Industry news, product updates, videos, infographics, and more from CIS
Filter
637 Results Found
Solutions
Industry
421 - 430 of 637 results
Published on 11.24.2020
Cloud service providers (CSPs) have changed the way organizations of all sizes architect and deploy their IT environments. CSPs now make it possi...
CIS BenchmarksCIS Hardened Images
Published on 11.23.2020
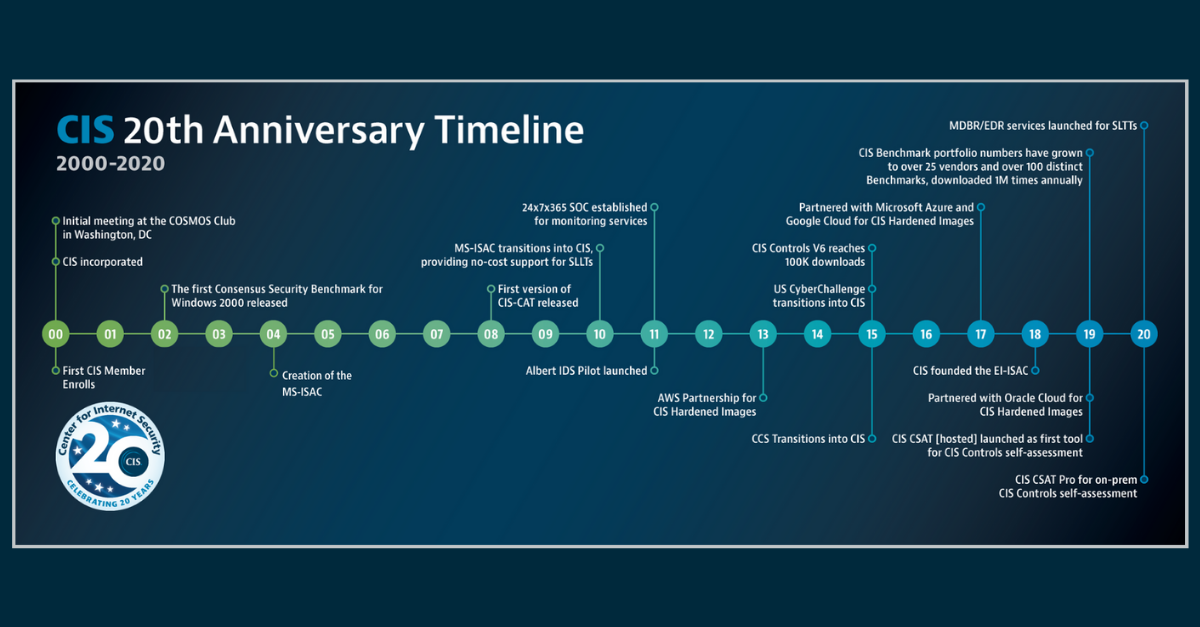
This year, the Center for Internet Security (CIS) is celebrating 20 years of making the connected world a safer place for people, businesses, and...
CIS BenchmarksCIS ControlsCIS Hardened ImagesCIS ServicesCIS SecureSuite
Published on 11.20.2020
This year, the Center for Internet Security (CIS) celebrated its 20th anniversary and also welcomed the 10,000th member to the Multi-State Inform...
MS-ISAC
Published on 11.18.2020
This year, the Center for Internet Security (CIS) is celebrating its 20th anniversary. It’s been 20 years of making the connected world a safer p...
CIS BenchmarksCIS SecureSuite
Published on 11.18.2020
The CIS Controls Self Assessment Tool (CIS CSAT) allows organizations to assess their implementation of the CIS Controls, enabling them to track ...
CIS Controls
Published on 11.17.2020
CIS continues to bring security to the cloud with virtual machine images pre-configured to the recommendations of the CIS Benchmarks. There are m...
CIS Hardened Images
Published on 11.16.2020
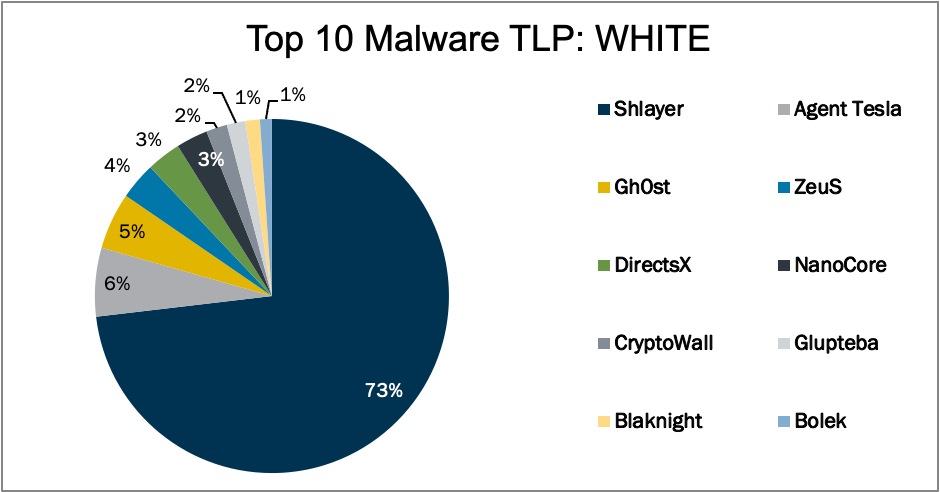
In October 2020, the MS-ISAC observed two malware (Bolek and NanoCore) return to the Top 10, as well as two new variants (DirectsX and Glupteba) ...
MS-ISAC
Published on 11.16.2020
This month brings several new CIS Benchmarks as well as new guidance for teleconferencing. These CIS Benchmark releases would not have been possi...
CIS BenchmarksCIS SecureSuite
Published on 11.05.2020
Increased demand for remote work capabilities continues throughout 2020. Customer security in the cloud remains an important part of that growth....
CIS BenchmarksCIS Hardened Images
Published on 11.04.2020
With hundreds of recommendations in each CIS Benchmark, automated assessment is the key to faster implementation of secure configuration at scale...
CIS BenchmarksCIS SecureSuite
Explore Related Cybersecurity Solutions

Safeguard IT systems against cyber threats with more than 100 configuration guidelines across more than 25 vendor product families.
Learn MoreProtect your organization from cyber-attacks with globally recognized CIS Controls, companion guides, and mappings.
Learn MoreCIS CyberMarket
Learn MoreCIS Hardened Images
Learn MoreCIS SecureSuite
Learn MoreCIS Services
Learn MoreAccess resources for threat prevention, protection, response, and recovery for U.S. State, Local, Tribal, and Territorial (SLTT) government entities.
Learn MoreAccess resources for threat prevention, protection, response, and recovery for U.S. State, Local, Tribal, and Territorial (SLTT) government entities.
Learn More