Blog Posts
Industry news, product updates, videos, infographics, and more from CIS
Filter
634 Results Found
Solutions
Industry
471 - 480 of 634 results
Published on 03.30.2020
Google Cloud announced general availability of its Shielded VMs (virtual machines) at a breakout session during Google Cloud Next ‘19. As a resul...
CIS Hardened Images
Published on 03.24.2020
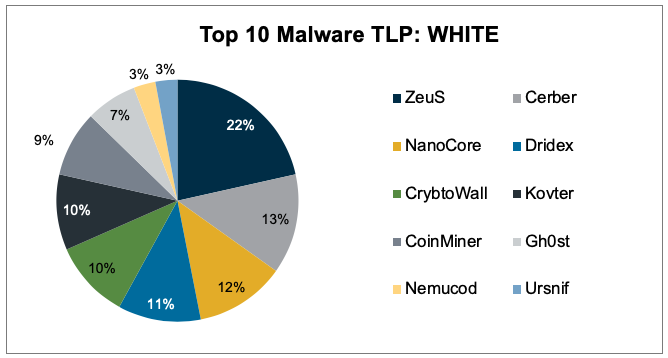
Top 10 Malware composition is very consistent with January 2020 with the exception of Ursnif. Nemucod remained, for the second month in a row, in...
MS-ISAC
Published on 03.19.2020
As the COVID-19 pandemic is forcing more and more companies to adjust their work schedules and move to telework environments, CIS remains committ...
CIS ControlsCIS SecureSuite
Published on 03.17.2020
Does your organization struggle to prepare for cybersecurity audits, sometimes juggling multiple requirements? If so, you’re not alone. CIS takes...
CIS BenchmarksCIS ControlsCIS SecureSuite
Published on 03.12.2020
With the COVID-19 (coronavirus) global pandemic, many employers are recommending additional telework to help keep employees safe and productive. ...
CIS Controls
Published on 03.09.2020
Reading a list of cybersecurity compliance frameworks is like looking at alphabet soup: NIST CSF, PCI DSS, HIPAA, FISMA, GDPR…the list goes on. I...
CIS BenchmarksCIS ControlsCIS SecureSuite
Published on 03.06.2020
The annual RSA Conference has become a rite of passage for cybersecurity professionals of all stripes. More than 45,000 people attended this year...
CIS BenchmarksCIS ControlsCIS SecureSuite
Published on 03.02.2020
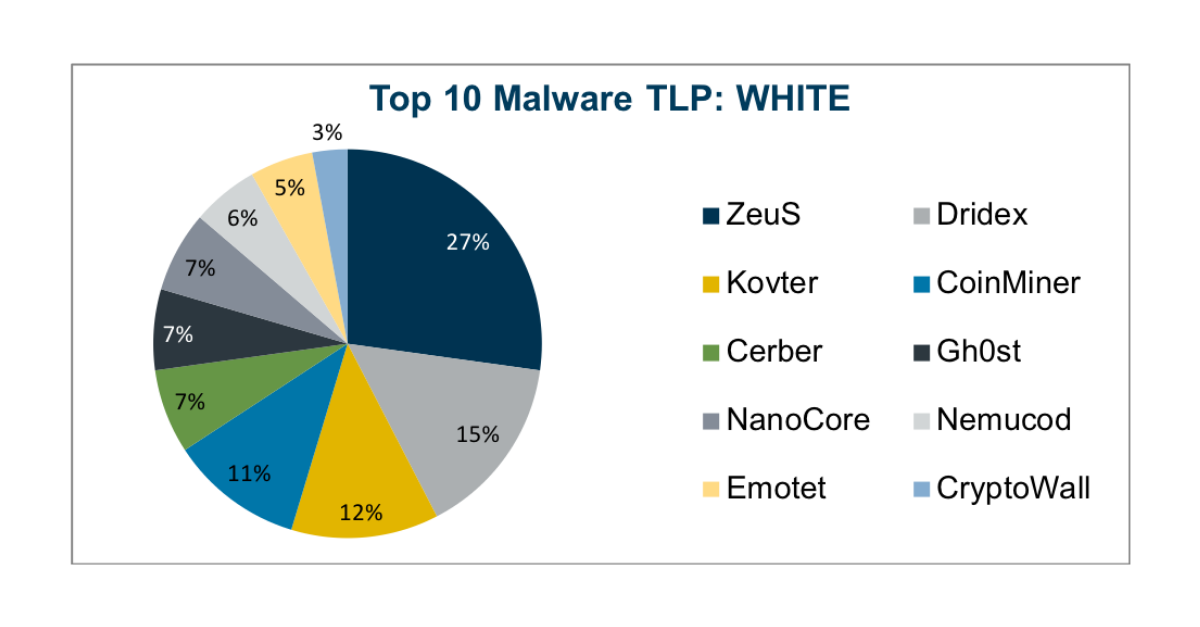
Top 10 Malware composition was very consistent with December 2019 with only a few new additions to the list. Of note Nemucod made an appearance i...
MS-ISAC
Published on 02.03.2020
Since their former life as the SANS Top 20, the CIS Controls have come a long way. The CIS Controls have grown over the years to help provide sec...
CIS Controls
Published on 01.30.2020
Securing the nation’s elections goes beyond the voting machines that are used to cast and tally ballots on Election Day. Electronic poll books, e...
Explore Related Cybersecurity Solutions

Safeguard IT systems against cyber threats with more than 100 configuration guidelines across more than 25 vendor product families.
Learn MoreProtect your organization from cyber-attacks with globally recognized CIS Controls, companion guides, and mappings.
Learn MoreCIS CyberMarket
Learn MoreCIS Hardened Images
Learn MoreCIS SecureSuite
Learn MoreCIS Services
Learn MoreAccess resources for threat prevention, protection, response, and recovery for U.S. State, Local, Tribal, and Territorial (SLTT) government entities.
Learn MoreAccess resources for threat prevention, protection, response, and recovery for U.S. State, Local, Tribal, and Territorial (SLTT) government entities.
Learn More