Blog Posts
Industry news, product updates, videos, infographics, and more from CIS
Filter
637 Results Found
Solutions
Industry
441 - 450 of 637 results
Published on 09.17.2020
Business Email Compromise Business Email Compromise (BEC), sometimes known as Email Account Compromise (EAC), is a common scam that leverages soc...
MS-ISAC
Published on 09.15.2020
The year 2020 will be remembered as the time when widespread internet-enabled remote working became a reality. IT administrators saw their respon...
CIS BenchmarksCIS SecureSuite
Published on 09.14.2020
CIS Amazon Web Services Foundations Benchmark v1.3.0 Prescriptive guidance for configuring security options for a subset of Amazon Web Services (...
CIS BenchmarksTechnology
Published on 09.02.2020
Oracle Cloud users have a new resource to help secure their cloud environments: the CIS Oracle Cloud Infrastructure Foundations Benchmark. This o...
CIS BenchmarksCIS Hardened Images
Published on 09.02.2020
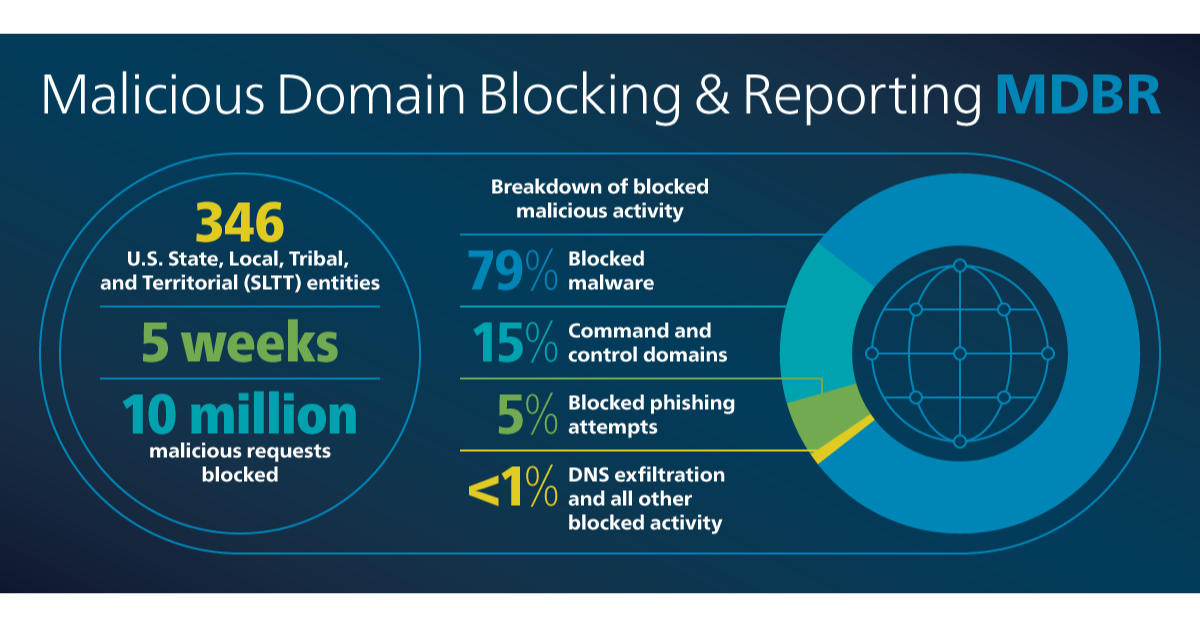
Malicious Domain Blocking and Reporting (MDBR) is the latest service that the Multi-State Information Sharing and Analysis Center (MS-ISAC) and E...
CIS ServicesMS-ISAC
Published on 08.21.2020
CIS Password Policy Guide The CIS Benchmarks Community has created a new CIS Password Policy Guide, with up-to-date best practices for creating p...
CIS BenchmarksTechnology
Published on 08.20.2020
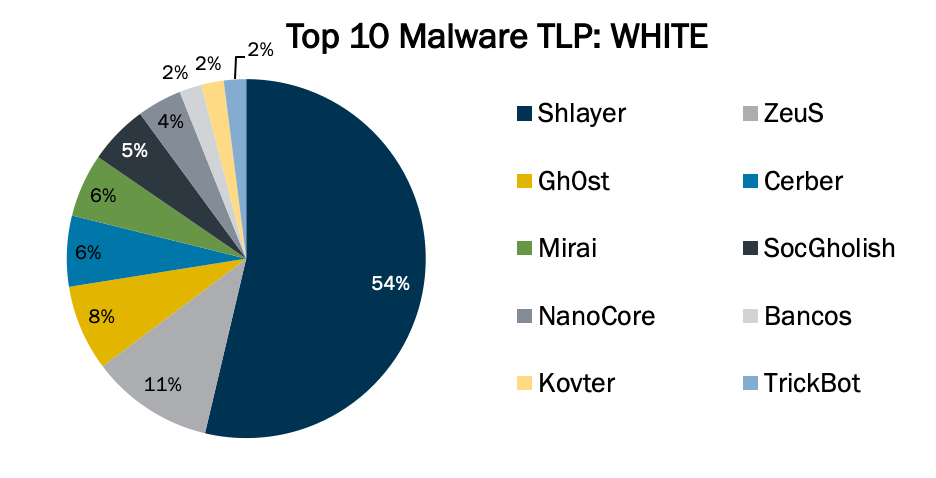
Top 10 Malware composition was consistent through July 2020, with the exception of Shlayer, Bancos, and TrickBot. The Top 10 Malware variants com...
MS-ISAC
Published on 08.18.2020
Basic cyber hygiene is the foundation for any good cybersecurity program. Tony Sager, CIS VP and Chief Evangelist, recently defined basic cyber h...
CIS ControlsCIS SecureSuite
Published on 08.13.2020
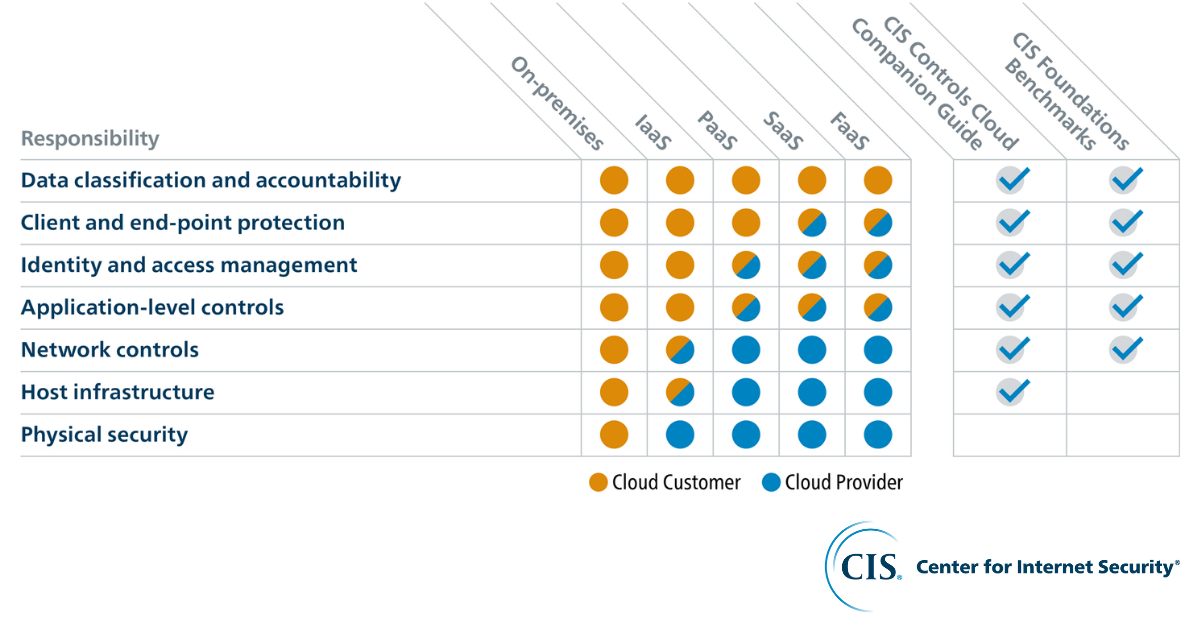
The shift to a global remote workforce is demonstrating just how difficult securing a cloud environment can be. This is especially true for organ...
CIS Hardened Images
Published on 08.11.2020
The Center for Internet Security (CIS) is proud to bring together so many of the world’s best IT security professionals in our community of volun...
CIS BenchmarksTechnology
Explore Related Cybersecurity Solutions

Safeguard IT systems against cyber threats with more than 100 configuration guidelines across more than 25 vendor product families.
Learn MoreProtect your organization from cyber-attacks with globally recognized CIS Controls, companion guides, and mappings.
Learn MoreCIS CyberMarket
Learn MoreCIS Hardened Images
Learn MoreCIS SecureSuite
Learn MoreCIS Services
Learn MoreAccess resources for threat prevention, protection, response, and recovery for U.S. State, Local, Tribal, and Territorial (SLTT) government entities.
Learn MoreAccess resources for threat prevention, protection, response, and recovery for U.S. State, Local, Tribal, and Territorial (SLTT) government entities.
Learn More