Blog Posts
Industry news, product updates, videos, infographics, and more from CIS
Filter by Topic
586 Results Found
341 - 350 of 586 results
Published on 02.25.2021
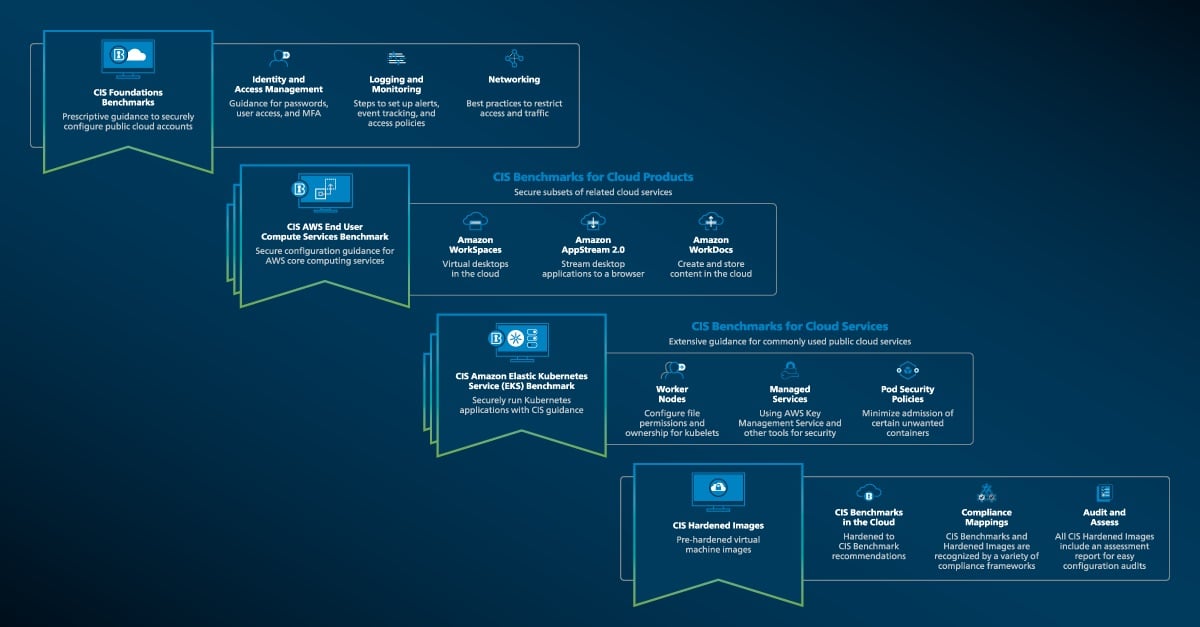
Secure Cloud Products and Services with New CIS BenchmarksThe cloud continues to expand with new products and services constantly introduced by cloud service providers (CSPs). The Center for Internet Sec...
Published on 02.24.2021
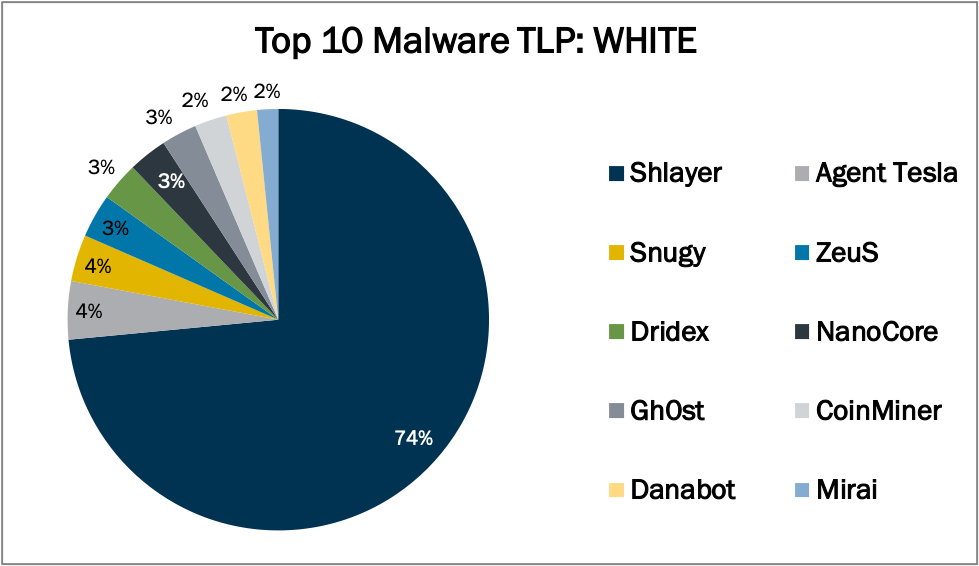
Top 10 Malware January 2021In January 2021, the MS-ISAC observed CoinMiner’s return to the Top 10, while Danabot made its first appearance. The Top 10 Malware variants make...
Published on 02.22.2021
5 Cybersecurity Hurdles Facing Public Sector (SLTT) CISOs (and 5 Way to Help)Public sector Chief Information Security Officers (CISOs) face the same challenges as their private sector counterparts, but with the additional ...
Published on 02.16.2021
Defending U.S. Hospitals Against Today’s Cyber ThreatsThe cost of cyber crime is often calculated in terms of financial loss, inconvenience, or reputational damage. But when it comes to health and ho...
Published on 02.12.2021
What You Need to Know About the CIS CSAT Pro v1.4.0 UpdatesThe CIS Controls Self Assessment Tool (CIS CSAT) allows organizations to perform assessments on their implementation of the CIS Controls. This en...
Published on 02.11.2021
Where Does Zero Trust Begin and Why is it Important?By: Kathleen M. Moriarty, CIS Chief Technology Officer Zero trust is an important information security architectural shift. It brings us away fro...
Published on 02.04.2021
Enhancing Security Through Collaboration on Azure CloudMicrosoft Azure customers now have access to a new version of the CIS Microsoft Azure Foundations Benchmark to help safeguard their cloud environ...
Published on 02.03.2021
CIS Benchmarks February 2021 UpdateCIS is excited to announce the release of the following CIS Benchmarks. These CIS Benchmark releases would not have been possible without the tim...
Published on 02.02.2021
CIS Benchmarks Communities: Where Configurations Meet ConsensusHave you ever wondered how technology hardening guidelines are developed? Some are determined by a particular vendor or driven by a bottom-line p...
Published on 02.02.2021
6 Simple Tips for Securing IoT DevicesIoT devices have become features in our homes and businesses, like connected kitchen gadgets, security monitoring systems, and drones. Read on to...
Explore Related Cybersecurity Solutions

Safeguard IT systems against cyber threats with more than 100 configuration guidelines across more than 25 vendor product families.
Learn MoreProtect your organization from cyber-attacks with globally recognized CIS Controls, companion guides, and mappings.
Learn MoreCIS CyberMarket
Learn MoreCIS Hardened Images
Learn MoreCIS SecureSuite
Learn MoreCIS Services
Learn MoreAccess resources for threat prevention, protection, response, and recovery for U.S. State, Local, Tribal, and Territorial (SLTT) government entities.
Learn MoreAccess resources for threat prevention, protection, response, and recovery for U.S. State, Local, Tribal, and Territorial (SLTT) government entities.
Learn More