Blog Posts
Industry news, product updates, videos, infographics, and more from CIS
Filter
637 Results Found
Solutions
Industry
431 - 440 of 637 results
Published on 10.26.2020
Videoconferencing has become a routine part of everyday life for remote workers, students, and families. Yet widespread adoption of this technolo...
CIS Benchmarks
Published on 10.20.2020
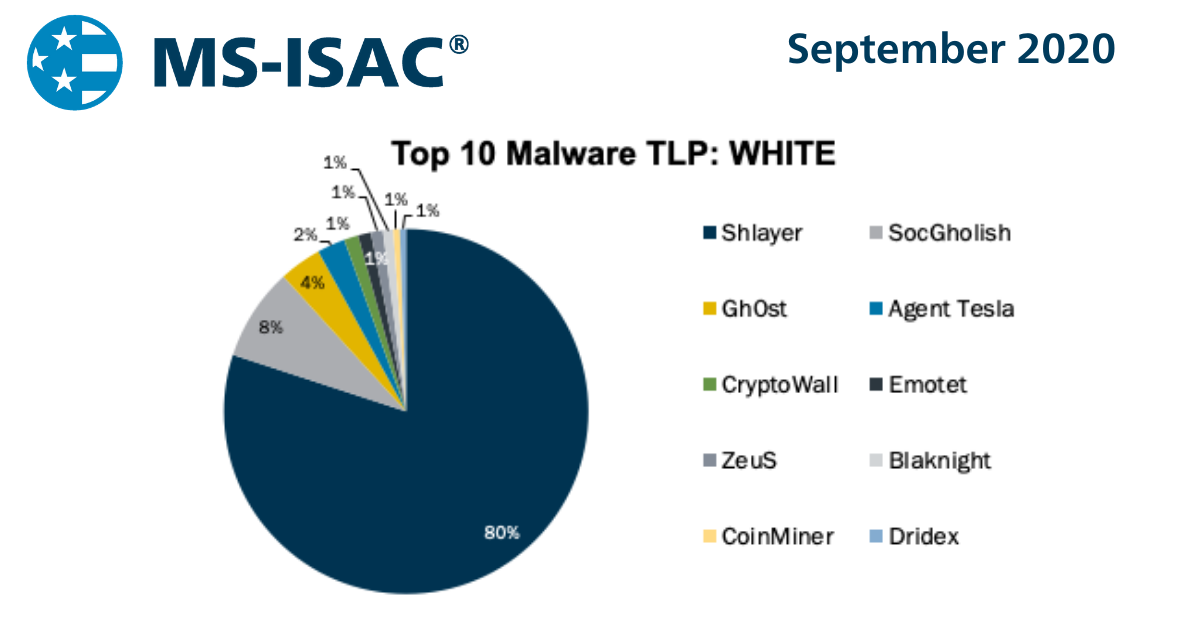
In September 2020, we had 3 malware return to the Top 10: CoinMiner, CryptoWall, and Emotet. The Top 10 Malware variants composed 87% of Total Ma...
MS-ISAC
Published on 10.15.2020
A version of this content first appeared in the TripWire’s “The State of Security“ blog. The term “best practice” often comes up in tandem with...
CIS Controls
Published on 10.14.2020
CIS is excited to announce the release of the following CIS Benchmarks. These CIS Benchmark releases would not have been possible without the tim...
CIS BenchmarksCIS SecureSuite
Published on 10.05.2020
The CIS Controls Self Assessment Tool (CIS CSAT) Pro allows organizations to assess their implementation of the CIS Controls, enabling them to tr...
CIS ControlsCIS SecureSuite
Published on 09.30.2020
In an earlier article, I wrote about the importance of cyber hygiene and offered up a specific definition of basic cyber hygiene based on CIS Con...
CIS Controls
Published on 09.29.2020
Do Your Part. Be Cyber Smart. In October in the United States, we recognize Cybersecurity Awareness Month, a concerted effort to raise awareness ...
CIS BenchmarksCIS SecureSuite
Published on 09.29.2020
At the Center for Internet Security (CIS) we have the privilege of working with some of the brightest minds in cybersecurity through our voluntee...
CIS BenchmarksTechnology
Published on 09.28.2020
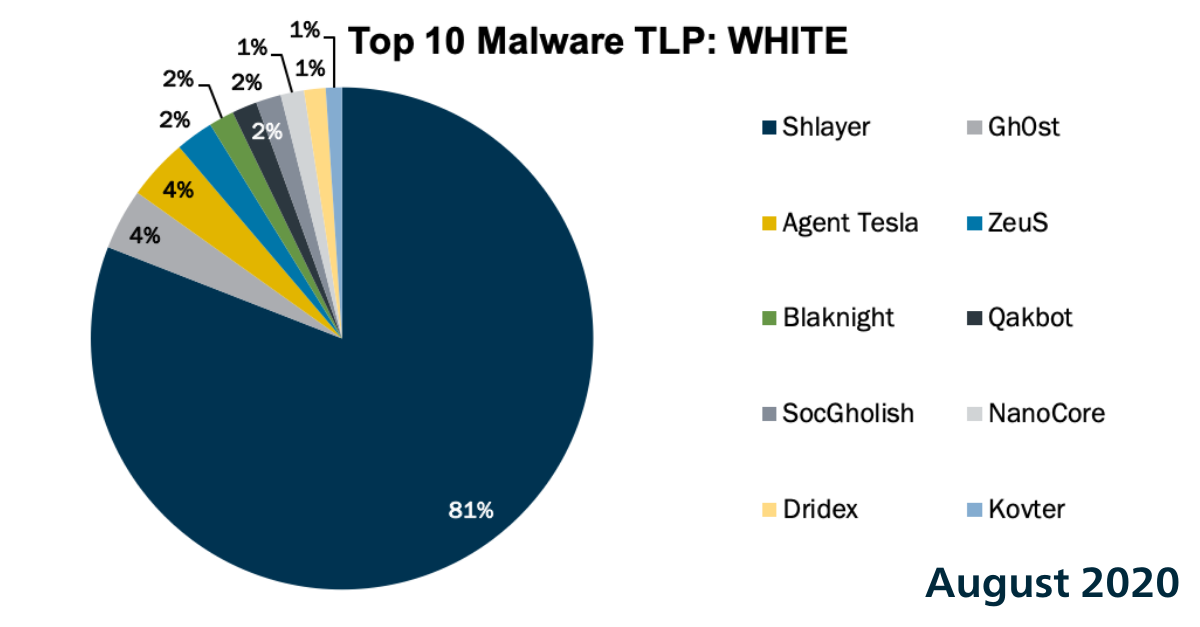
In August 2020, we had 4 new malware enter the Top 10 with two of them being first-timers on the list, Agent Tesla and Blaknight. The Top 10 Malw...
MS-ISAC
Published on 09.21.2020
Cyber threats are constantly evolving. As recently as 2016, Trojan malware accounted for nearly 50% of all breaches. Today, they are responsible ...
CIS BenchmarksCIS SecureSuite
Explore Related Cybersecurity Solutions

Safeguard IT systems against cyber threats with more than 100 configuration guidelines across more than 25 vendor product families.
Learn MoreProtect your organization from cyber-attacks with globally recognized CIS Controls, companion guides, and mappings.
Learn MoreCIS CyberMarket
Learn MoreCIS Hardened Images
Learn MoreCIS SecureSuite
Learn MoreCIS Services
Learn MoreAccess resources for threat prevention, protection, response, and recovery for U.S. State, Local, Tribal, and Territorial (SLTT) government entities.
Learn MoreAccess resources for threat prevention, protection, response, and recovery for U.S. State, Local, Tribal, and Territorial (SLTT) government entities.
Learn More