Blog Posts
Industry news, product updates, videos, infographics, and more from CIS
Filter by Topic
586 Results Found
471 - 480 of 586 results
Published on 04.23.2019
A Day in the Life of a Computer Emergency Response Team (CIRT) ManagerHelping U.S. State, Local, Tribal, and Territorial (SLTT) government entities respond to cyber incidents on a daily basis can be intense, but Val...
Published on 04.04.2019
V7.1 Introduces Implementation Groups to the CIS Critical Security Controls™The CIS Critical Security Controls are internationally-recognized cybersecurity best practices for defense against common threats. They are a co...
Published on 04.02.2019
6 Reasons it’s Smart to Work in the CloudCIS Chief Technology Officer Brian Calkin predicted in our 2019 cybersecurity trends blog that organizations would continue to move to the cloud....
Published on 04.01.2019
SCAP 2.0, The Time Is NowBy Curtis Dukes, Executive VP and GM – CIS Security Best Practices Admonitions to try harder and spend more on cybersecurity will not prevent mor...
Published on 03.21.2019
A Day in the Life with a Principal Software EngineerAt CIS, we have a team of our experts working with a global community of cybersecurity professionals. Together, they help develop tools and resou...
Published on 03.12.2019
3 Steps to Deploying a Hardened OS by TailoringIf you’re looking for the ideal machine image template, get ready to do a little customization. A custom configuration policy is needed whenever ...
Published on 03.07.2019
New Release: CIS Controls™ Mobile Companion GuideThe CIS Controls team has released a new companion guide to help organizations break down and map the applicable CIS Controls and their implement...
Published on 02.28.2019
Version 7.1 – A new way to look at the CIS Critical Security ControlsThe CIS Critical Security Controls are internationally-recognized for bringing together expert insight about threats, business technology, and de...
Published on 02.26.2019
A Day in the Life with a Sr. Account Management SpecialistCIS® is home to the Multi-State Information Sharing and Analysis Center® (MS-ISAC®). It’s the go-to resource for cyber threat prevention, protect...
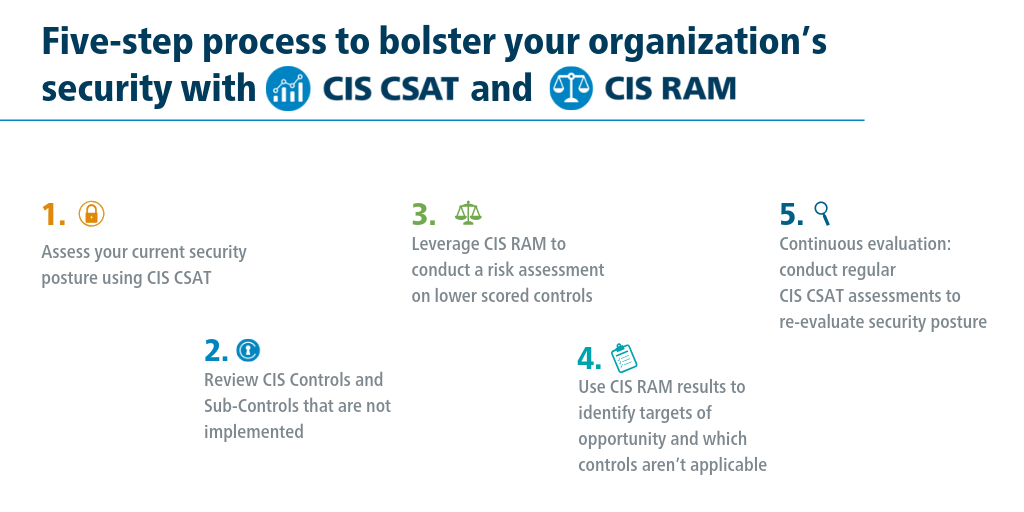
Published on 02.21.2019
Assessing Risk and Security Posture with CIS Controls ToolsBy Sean Atkinson, Chief Information Security Officer, and Phil Langlois, CIS Controls Technical Product Manager The CIS Controls are used by orga...
Explore Related Cybersecurity Solutions

Safeguard IT systems against cyber threats with more than 100 configuration guidelines across more than 25 vendor product families.
Learn MoreProtect your organization from cyber-attacks with globally recognized CIS Controls, companion guides, and mappings.
Learn MoreCIS CyberMarket
Learn MoreCIS Hardened Images
Learn MoreCIS SecureSuite
Learn MoreCIS Services
Learn MoreAccess resources for threat prevention, protection, response, and recovery for U.S. State, Local, Tribal, and Territorial (SLTT) government entities.
Learn MoreAccess resources for threat prevention, protection, response, and recovery for U.S. State, Local, Tribal, and Territorial (SLTT) government entities.
Learn More