Blog Posts
Industry news, product updates, videos, infographics, and more from CIS
Filter
637 Results Found
Solutions
Industry
351 - 360 of 637 results
Published on 07.13.2021
In May 2021, the CIS-CAT development team delivered CIS-CAT Pro Assessor v4.7.0 with the latest CIS Benchmark automated assessment content. The t...
CIS BenchmarksCIS SecureSuite
Published on 07.08.2021
The Center for Internet Security (CIS) has released three new CIS Hardened Images. CIS built two of these new hardened virtual machines (VMs) on ...
CIS BenchmarksCIS Hardened Images
Published on 07.07.2021
This month’s list may be short, but it is mighty! These CIS Benchmark releases would not have been possible without the time and support of commu...
CIS BenchmarksCIS SecureSuite
Published on 07.01.2021
The Center for Internet Security (CIS) recently celebrated 20 years of bringing confidence to the connected world with consensus-based security g...
CIS BenchmarksCIS SecureSuite
Published on 06.29.2021
Cyber hygiene and patching are key measures towards protecting data and systems. However, it’s not always possible or practical to patch when vul...
CIS BenchmarksCIS Controls
Published on 06.23.2021
The CIS Benchmarks Community on CIS WorkBench is made up of subject matter experts, vendors, technical writers, and CIS SecureSuite Members from ...
CIS BenchmarksTechnology
Published on 06.21.2021
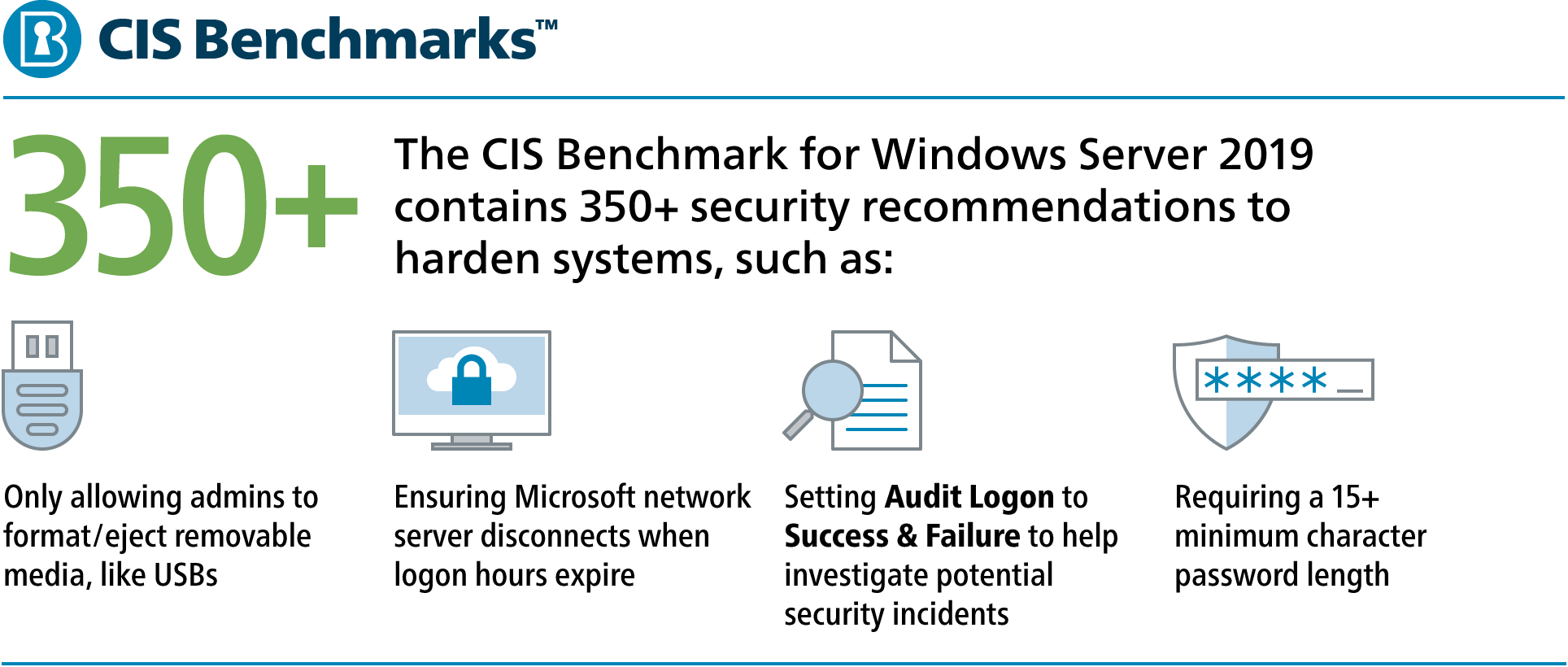
Cloud security is just as vital as on-premises security. Hundreds of security recommendations may exist to harden your Operating Systems (OS). Th...
CIS BenchmarksCIS Hardened ImagesCIS SecureSuite
Published on 06.17.2021
What does your cloud configuration look like? In many organizations, moving workloads to the cloud creates a more elastic technology infrastructu...
CIS BenchmarksCIS Hardened Images
Published on 06.16.2021
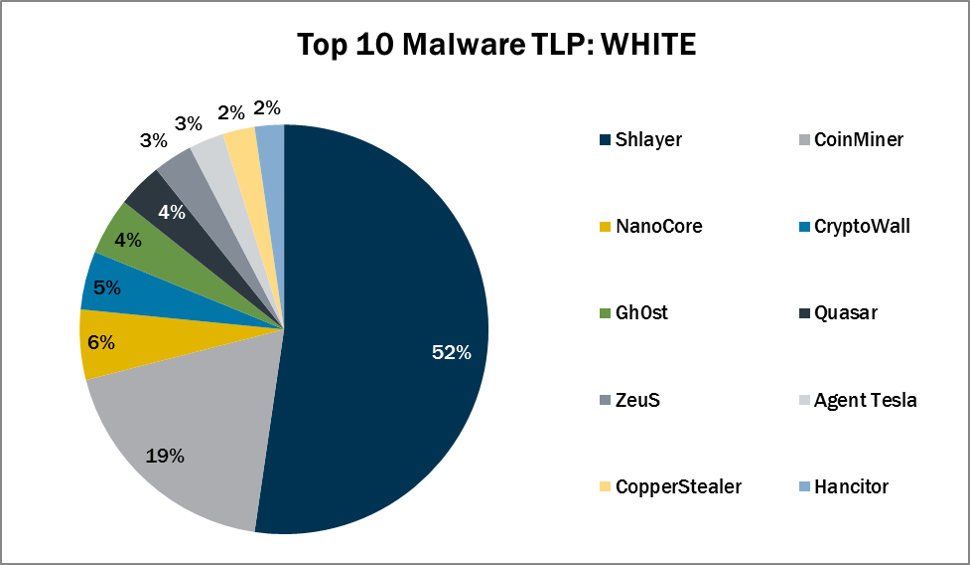
In May 2021, the MS-ISAC observed Quasar’s return to the Top 10. The Top 10 Malware variants comprise 75% of the total malware activity in May 20...
MS-ISAC
Published on 06.14.2021
Many offices are opening their doors and welcoming employees back to the workplace for the first time since the COVID-19 pandemic started. The tr...
CIS Controls
Explore Related Cybersecurity Solutions

Safeguard IT systems against cyber threats with more than 100 configuration guidelines across more than 25 vendor product families.
Learn MoreProtect your organization from cyber-attacks with globally recognized CIS Controls, companion guides, and mappings.
Learn MoreCIS CyberMarket
Learn MoreCIS Hardened Images
Learn MoreCIS SecureSuite
Learn MoreCIS Services
Learn MoreAccess resources for threat prevention, protection, response, and recovery for U.S. State, Local, Tribal, and Territorial (SLTT) government entities.
Learn MoreAccess resources for threat prevention, protection, response, and recovery for U.S. State, Local, Tribal, and Territorial (SLTT) government entities.
Learn More