Blog Posts
Industry news, product updates, videos, infographics, and more from CIS
Filter
633 Results Found
Solutions
Industry
321 - 330 of 633 results
Published on 10.14.2021
The Center for Internet Security (CIS) and the Multi-State Sharing and Analysis Center (MS-ISAC) are proudly serving as partners for the Virtual ...
MS-ISAC
Published on 10.13.2021
U.S. State, Local, Tribal, and Territorial (SLTT) organizations face a stark challenge in mounting a proper cybersecurity defense against malicio...
CIS ServicesMS-ISAC
Published on 10.07.2021
By Tony Sager, CIS Sr. Vice President and Chief Evangelist The conversation that eventually led to the CIS Critical Security Controls started wit...
CIS Controls
Published on 10.06.2021
Contingency plans in cybersecurity are essential when preparing for any incident, whether it is malware infecting an end user’s hard drive or ran...
MS-ISAC
Published on 10.06.2021
It’s obvious that the remote capabilities of the modern day office have transformed permanently. Most organizations will see an increase in hybri...
CIS BenchmarksCIS Hardened Images
Published on 10.06.2021
The following CIS Benchmark updates have been released. We’ve highlighted the major updates below. Each Benchmark includes a full changelog that...
CIS BenchmarksCIS SecureSuite
Published on 10.05.2021
For 18 years, the Cybersecurity and Infrastructure Security Agency (CISA) and the National Cyber Security Alliance (NCSA) have teamed up to promo...
CIS SecureSuite
Published on 10.04.2021
The CIS Controls Self Assessment Tool (CIS CSAT) allows organizations to perform assessments on their implementation of the CIS Critical Security...
CIS SecureSuite
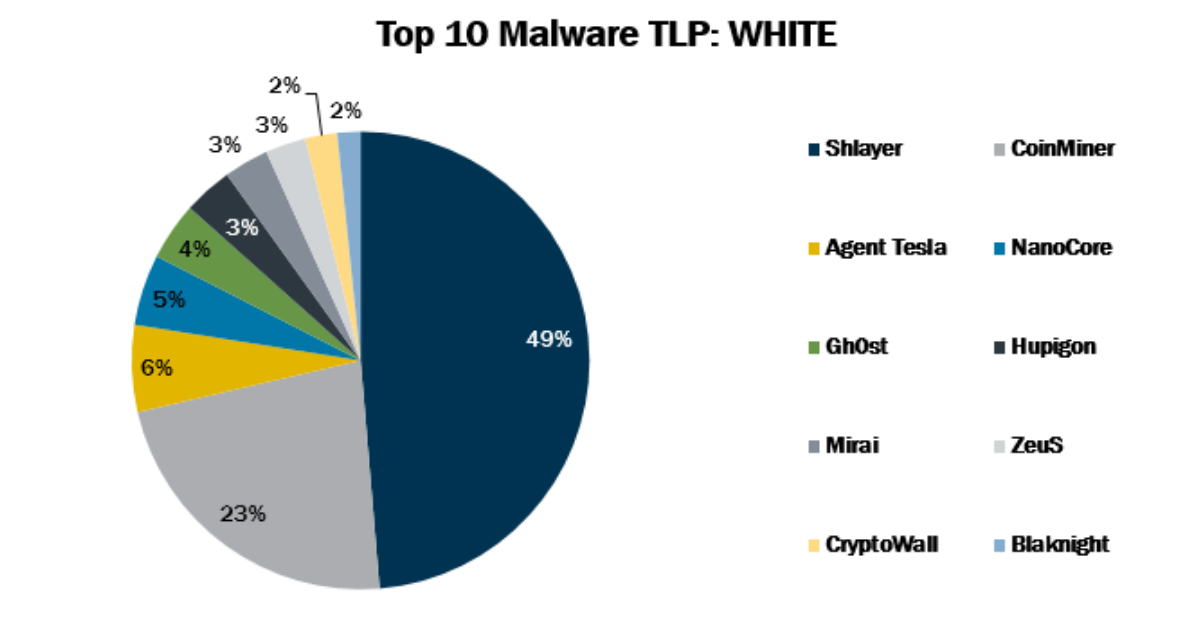
Published on 10.01.2021
In August 2021, the MS-ISAC observed Blaknight’s return to the Top 10 Malware along with Hupigon, which made its first appearance in the Top 10. ...
MS-ISAC
Published on 09.29.2021
The Center for Internet Security (CIS) Community Defense Model (CDM) v2.0 can be used to design, prioritize, implement, and improve an enterprise...
CIS Controls
Explore Related Cybersecurity Solutions

Safeguard IT systems against cyber threats with more than 100 configuration guidelines across more than 25 vendor product families.
Learn MoreProtect your organization from cyber-attacks with globally recognized CIS Controls, companion guides, and mappings.
Learn MoreCIS CyberMarket
Learn MoreCIS Hardened Images
Learn MoreCIS SecureSuite
Learn MoreCIS Services
Learn MoreAccess resources for threat prevention, protection, response, and recovery for U.S. State, Local, Tribal, and Territorial (SLTT) government entities.
Learn MoreAccess resources for threat prevention, protection, response, and recovery for U.S. State, Local, Tribal, and Territorial (SLTT) government entities.
Learn More