Blog Posts
Industry news, product updates, videos, infographics, and more from CIS
Filter by Topic
582 Results Found
311 - 320 of 582 results
Published on 05.11.2021
5 Cloud Computing Benefits: Why You Should Work in the CloudWhat are the benefits of cloud computing? Many organizations find that cloud service providers (CSPs) can meet their needs while providing a numb...
Published on 05.06.2021
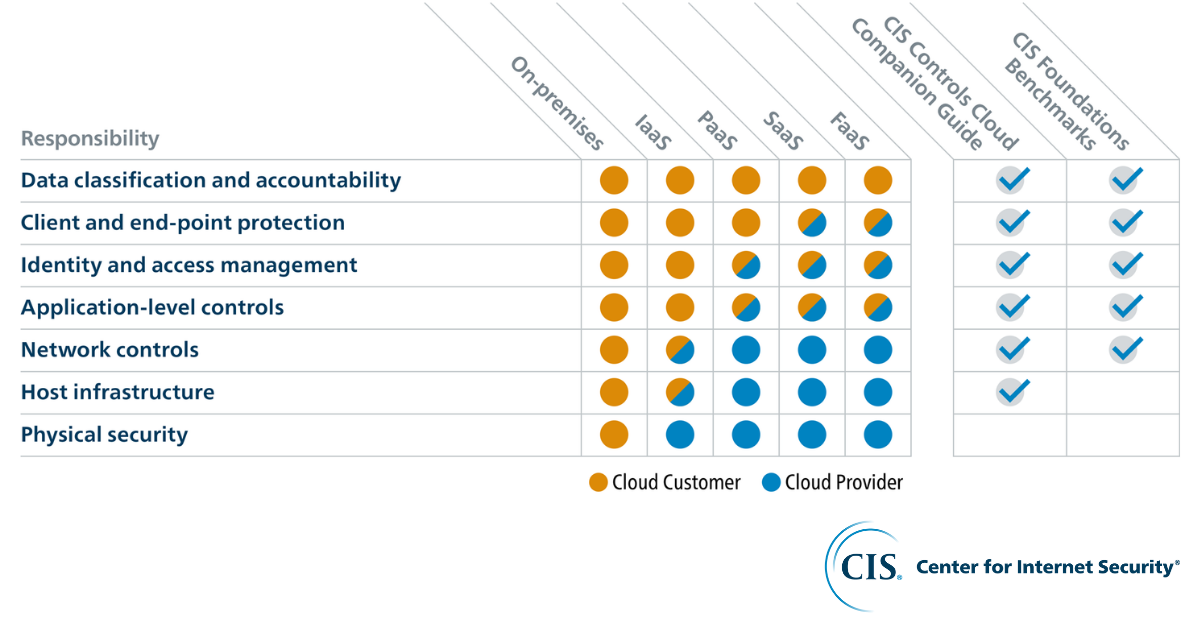
Meet Your Shared Security Responsibility on AWS with CISGartner forecasts that global public cloud end user spending will grow 23% in 2021. With the continuous increase in cloud computing, cloud securi...
Published on 05.05.2021
CIS Benchmarks May 2021 UpdateWe’re excited to announce our CIS Benchmarks May 2021 updates. These CIS Benchmark releases would not have been possible without the time and sup...
Published on 05.04.2021
CIS Controls v8 at (Virtual) RSA Conference 2021!The Center for Internet Security (CIS) is excited to be part of RSA Conference 2021 – the world’s leading information security conference and exp...
Published on 04.29.2021
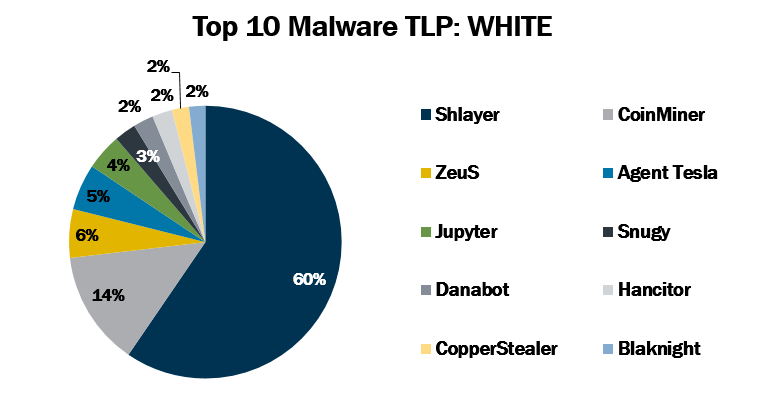
Top 10 Malware March 2021In March 2021, the MS-ISAC observed Blaknight and Danabot’s return to the Top 10, while CopperStealer made its first appearance. The Top 10 Malwa...
Published on 04.27.2021
STIG Compliance with CIS AWS Cloud Security ResourcesSecuring your IT infrastructure can be a challenge, especially if you’re working in a regulated environment. Many compliance frameworks like, Def...
Published on 04.26.2021
Avoid Configuration Drift Through Effective MonitoringOnce your organization is secured, you’ll need to ensure that your environment doesn’t stray from its protected state. Configuration drift may be...
Published on 04.22.2021
5 Tips to Harden Your OS On-Prem or in the CloudCloud security is just as vital as on-premises security. Hundreds of security recommendations may exist to harden your Operating Systems (OS). Th...
Published on 04.21.2021
Ransomware: The Data Exfiltration and Double Extortion TrendsPart 3 in a series on Malware Overview The Multi-State Information Sharing and Analysis Center’s (MS-ISAC) Cyber Threat Intelligence (CTI) team a...
Published on 04.19.2021
Managing Your Cybersecurity Program for the WinNo matter an organization’s size or complexity, cybersecurity is a team sport. Departments and individuals across the board have a stake in ensur...
Explore Related Cybersecurity Solutions

Safeguard IT systems against cyber threats with more than 100 configuration guidelines across more than 25 vendor product families.
Learn MoreProtect your organization from cyber-attacks with globally recognized CIS Controls, companion guides, and mappings.
Learn MoreCIS CyberMarket
Learn MoreCIS Hardened Images
Learn MoreCIS SecureSuite
Learn MoreCIS Services
Learn MoreAccess resources for threat prevention, protection, response, and recovery for U.S. State, Local, Tribal, and Territorial (SLTT) government entities.
Learn MoreAccess resources for threat prevention, protection, response, and recovery for U.S. State, Local, Tribal, and Territorial (SLTT) government entities.
Learn More